Multi-factor Authentication vs. Single-factor Authentication: Safeguarding Your Digital World
December 4, 2023
Due to our society's increasing interconnection, protecting one's digital identity has become increasingly important. The authentication approach is often regarded as the most crucial component of information security since it serves to authenticate an individual's stated identity. The most often used authentication mechanisms are multi-factor authentication (MFA) and single-factor authentication (SFA).
- Single-factor Authentication (SFA): The traditional SFA authentication method, is based on a single, commonly recognized piece. Individuals may recognize, or have easy access to, this specific element. The data in question could be a personal identification number (PIN), a password, or any other type of information that is unique to the person doing the authentication.
- Multi-factor Authentication (MFA): As its name would suggest, MFA requires two or more factors for access. For this reason MFA is regarded preferable to SFA for enhanced security. The attributes of authentication are typically classified into three main groups: possession (also known as ownership), knowledge (also known as cognition), and biometric (also known as intrinsic traits).
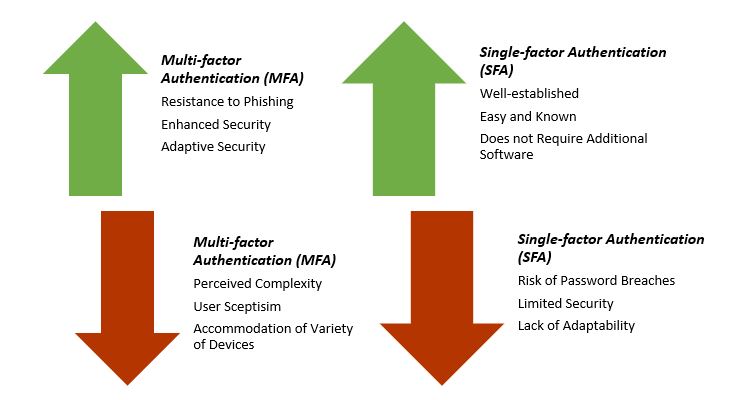
To protect the security of one's online presence, it is critical to have a thorough grasp of the advantages and disadvantages between the many solutions accessible. A brief comparison analysis of the benefits and downsides of these authentication methods warrants a self-evident conclusion: SFA is the most viable authentication approach but has the most drawbacks.
Single-factor Authentication (SFA): The Weakest Link
SFA is the most viable authentication approach due to its simplicity. Users are only required to enter a single piece of information, such as a password, in order to obtain access to their accounts. Despite its widespread acceptance and ease of use, SFA has some important drawbacks:
- Risk of Password Breaches: The weakness in SFA's security is its password management system. Passwords have become a prominent target for hackers due to their susceptibility to misuse, theft, or compromise via data intrusions. If a password is overly simple or commonly used, its strength may be undermined.
- Limited Security: Because of its single ingredient, SFA can only provide limited protection. If an adversary successfully discovers the password, obtaining unauthorized access would be simple.
- Lack of Adaptability: The SFA needs to react more effectively to the ever-changing terrain of developing issues. The current level of security needs to be improved to combat the two sophisticated attacks of credential stuffing and phishing.
In view of these urgent threats, businesses are rapidly adopting MFA as a more reliable security approach.
Multi-factor Authentication (MFA): Layered Security
Implementing MFA improves security by adding levels of protection to solve the shortcomings of SFA. When users must meet multiple conditions, enemies find it much more difficult to get unauthorized access. Additional benefits to MFA include:
- Enhanced Security: The use of MFA improves security by requesting the user to prompt multiple authentication factors at the same time. If a potential unauthorized user possesses only one of the crucial elements, such as a password, their ability to gain access to the system is reduced.
- Resistance to Phishing: When done correctly, MFA can effectively prevent fraudulent attempts. If the user unintentionally discloses their password, the offender will have difficulties accessing the account without additional verification measures, such as a fingerprint or a paired smartphone. Despite the possibility of password leakage, the use of these supplemental components is still required.
- Adaptive Security: The MFA program is capable of adapting and responding to various risk conditions. In the event a login attempt comes from a suspicious device or location, MFA can be enabled.
Common Mistakes in Installing Multi-Factor Authentication
Although MFA is recognized to considerably improve security, organizations should avoid making the following mistakes:
- Weak Recovery Processes: Employers have the burden of ensuring secure access to user accounts, even when one of the authentication components is unavailable. More mechanisms for recovering lost or stolen accounts may expose a system to security risks if not properly secured.
- Inadequate or Lack of Training: Inadequate MFA implementation can cause user confusion and displeasure. These difficulties can be avoided with proper user education. MFA program participants require extensive rules and thorough education.
- Limited Device Options: Companies must provide a comprehensive range of MFA device solutions in order to meet the diverse demands and preferences of their clientele. This requires several authentication methods such as text message codes, mobile authenticator apps, biometrics, and hardware tokens.
- Complexity of Implementation: The effectiveness of overly sophisticated MFA systems is likely to be reduced. When it comes to accessing their accounts, the smooth coexistence of security and usability should not impose additional costs on consumers.
Balancing Security and User Experience
MFA provides a strong security mechanism; nonetheless, organizations should remember the importance of addressing the user experience. Users are likely to be dissatisfied if MFA solutions prove difficult to use or involve an excessive number of steps. The ideal balance between user experience and data security is critical in the effective deployment of MFA.
Conclusion: The Power of Multi-Factor Authentication
MFA has evolved into a dependable protection for our digital identities in the digital world resulting from the rising diversity of cyberattacks. This is because MFA needs the confirmation of many data elements. MFA fortifies a system's defenses and boosts its resilience against a wide range of attacks by requiring the usage of several authentication factors.
Although single-element authentication is widely used, it is incapable of withstanding the frequent and sophisticated attacks that are common in today's culture. Therefore, MFA should be part of every individual's and organization's security policy.
References
Cherry, D. (2022). Multi-Factor Authentication. In Enterprise-Grade IT Security for Small and Medium Businesses: Building Security Systems, in Plain English (pp. 83–96). Berkeley, CA: Apress.
Karie, N. M., Kebande, V. R., Ikuesan, R. A., Sookhak, M., & Venter, H. S. (2020, March). Hardening SAML by Integrating SSO and Multi-Factor Authentication (MFA) in the Cloud. In Proceedings of the 3rd International Conference on Networking, Information Systems & Security (pp. 1–6).
Sharphathy, M. N., & Sumalatha, V. (2023, July). SSS-EC: Cryptographic-based Single-Factor Authentication for Fingerprint Data with Machine Learning Technique. In 2023 2nd International Conference on Edge Computing and Applications (ICECAA) (pp. 308–315). IEEE.
About the Author

Dr. Sabine Charles
Dr. Sabine Charles, CIA, CISA, CFE, CISM, "The CPA Doctor," is a celebrated leadership and personal development expert. She is the Chief Internal Auditor of the Touro College and University System. As the CEO of Charles Financial...
Read Full Author Bio

Dr. Sabine Charles
Dr. Sabine Charles, CIA, CISA, CFE, CISM, "The CPA Doctor," is a celebrated leadership and personal development expert. She is the Chief Internal Auditor of the Touro College and University System. As the CEO of Charles Financial Strategies and TAPA Institute, she channels her knowledge to aid personal and organizational success. With vast experience in auditing, research, teaching, and consulting, she's authored several books, including "Leadership MEQ."
Articles
Enhancing the Internal Audit Activity Through Emotional Intelligence
Multi-factor Authentication vs. Single-factor Authentication: Safeguarding Your Digital World