A Growing Trend: ESG Reporting for Higher Education Institutions
As they looked into their crystal balls for the year ahead, two organizations, Gartner and the Institute of Internal Auditors published lists of emerging risks for 2022. Not surprisingly, sustainability related to environmental and climate issues as well as social change made both lists.
These risks are just as relevant for public sector organizations, including higher education institutions, as they are for private and publicly held businesses, and they are only expected to grow in the years ahead.
Sustainability and social responsibility encompass a broad range of non-financial issues that may affect an organization’s financial condition and performance.
They may include environmental issues, such as the size of the organization’s carbon footprint, efforts to replace fossil fuels with renewable energy sources, and overall use of natural resources.
These responsibilities may also reference social issues, such as workplace diversity, health and safety, and consumer product safety risks.
What is Environmental, Social and Governance (ESG)?
As implied by its name, ESG reporting is concerned with measuring performance in three very different domains: environmental sustainability, social responsibility and governance. The key measures used to document and report performance will differ significantly from one organization to another, and more importantly, from traditional accounting measures focused on financial performance.
For now, much of the focus of ESG reporting is on the private sector, especially publicly traded companies subject to U.S. Securities and Exchange Commission (SEC) regulations. The SEC is currently considering several proposed regulations incorporating elements of ESG reporting into the financial reporting requirements for public companies.
That doesn’t mean government entities and higher education institutions are off the hook. Concerns about climate change, expanded opportunities in the workplace, and effective governance are not expected to recede any time soon. History shows us that the public sector is usually not far behind the private sector when issuing guidance and requirements in emerging risk areas. Moreover, the same sentiment driving change in the public sector will affect government entities and higher education institutions as constituents seek more accountability for sustainability issues.
Forward-thinking universities and other public sector organizations can start to implement the appropriate processes to be better prepared to comply with new requirements that emerge.
Metrics and Reporting for Higher Education: The STARS Framework
When it comes to sustainability issues, higher education is not exempt from public sentiment and pressure. In recent years, “green rankings” of universities in various leading publications, including The Princeton Review, have highlighted the importance stakeholders are placing on sustainability. The rankings are based on metrics and voluntary reporting by the institutions themselves.
While there are several frameworks available, the most widely used ESG reporting framework is the Sustainability Tracking, Assessment & Rating System (STARS). It is a self-reporting framework open to the full spectrum of higher education institutions, from community colleges to research universities.
STARS was created in 2006 by the Association for Advancement of Sustainability in Higher Education (AASHE) in collaboration with higher education institutions. Currently, more than one thousand institutions have registered to use the STARS reporting tool to:
- Provide a framework for understanding sustainability in all sectors of higher education.
- Enable meaningful comparisons over time and across institutions using a common set of measurements developed with broad participation from the international campus sustainability community.
- Create incentives for continual improvement toward sustainability.
- Facilitate information sharing about higher education sustainability practices and performance.
- Build a stronger, more diverse campus sustainability community.
The STARS framework includes long-term sustainability goals for already high-achieving institutions and entry points of recognition for institutions taking the first steps toward sustainability. Many institutions use STARS as a planning tool to identify areas of strength in sustainable practices and areas that need improvement. Each STARS report and rating is valid for up to three years, and a report may be submitted as often as once per year.
The framework is made up of five categories: Academics (AC), Engagement (EN), Operations (OP), Planning & Administration (PA) and Innovation & Leadership (IN), and these are broken into sub-categories for reporting purposes:
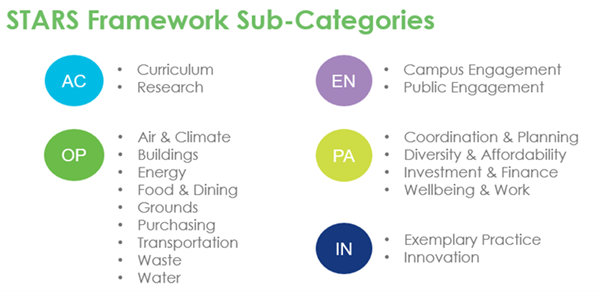
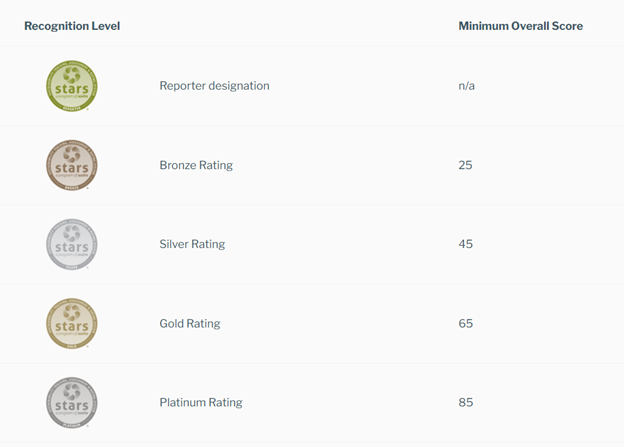
Each category is broken down into credits with specific metrics, activities, or practices needed to earn these credits. The institution identifies which credits they will pursue and collects the information from campus stakeholders. The institution accumulates points based on these practices and receives a rating of platinum, gold, silver, or bronze based on the number of points awarded. 
Below is an example of how one institution, the University of Georgia, appears in the STARS system. To allow institutions to compare their sustainability with others, the data used to assign points are made public.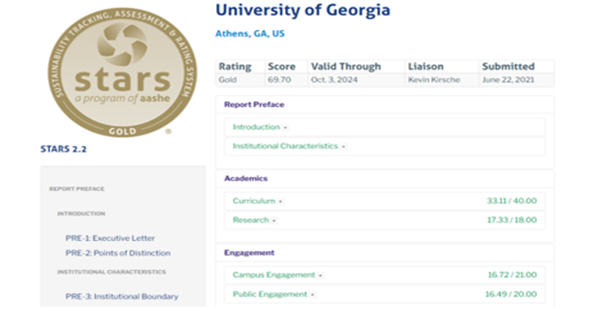
Audit Committee and CAE Considerations
When it comes to ESG reporting, we have found that common questions arise among boards and audit committees as they consider the implications for their institution. These include:
- Have we assessed the ESG disclosure criteria and determined which information is most relevant?
- Do we have a strategy for identifying which ESG information is available?
- How does our ESG performance relate to our institutional strategies and objectives?
- Are our processes designed to produce accurate and complete information for our stakeholders?
- Who is responsible for defining our institutional ESG strategy and overseeing information gathering through disclosure?
On a somewhat granular level, Chief Audit Executives and other audit leaders have questions related to ESG and reporting and disclosure. These include:
- Do we have a published ESG or sustainability report or other available information? If so, is it still up to date and fit for purpose?
- Is our ESG strategy aligned with our institutional objectives and long-term strategy? Does that strategy clearly state our ESG goals?
- Who is responsible for overseeing the development and execution of the ESG program?
- Have we defined the key metrics and data to quantitatively measure ESG performance across our institution?
- Do we have defined, consistent processes and controls to identify, gather, aggregate and publish key ESG performance indicators?
- Does our ESG/Sustainability strategy leverage one of the common reporting frameworks, and are we obtaining independent assurance or other support?
How the Audit Team Can Support ESG Efforts and Build Opportunities
For the audit team, it makes sense to approach ESG from a risk management perspective. In addition, contributing to the organization’s ESG efforts helps add value to the organization. The Internal Audit (IA) department can take these steps as part of the overall ESG program:
- Request an ESG risk assessment for the institution.
- In gathering information for STARS reports or other ESG disclosures, focus on adopting an enterprise-wide approach to managing ESG risks.
- Educate the administration about ESG reporting and the role organizational governance plays in the evaluation process.
- Identify and propose solutions to facilitate sharing information across siloed and decentralized approaches to risk management.
- Promote IA’s role in providing independent assurance.
IA can anticipate emerging ESG disclosure expectations and requirements by encouraging and understanding processes and controls in the institution. IA can also advocate for the adoption of established ESG frameworks and relevant, data-driven reporting, help to assess institutional stakeholders’ expectations and gaps in currently disclosed information, and support process-integrity of reporting by assessing how key data is compiled and reported.
Looking Ahead
As higher education institutions of all types and sizes continue to adopt and embrace ESG reporting, internal auditors will have an important role in helping to lay the groundwork for success. They have an opportunity to play a key role in improving internal controls and the overall adoption of these processes. The risks are unlikely to go away any time soon. The important thing will be the way institutions prepare for them.